Social Media Security: Vulnerabilities to Look Out for in 2023
With social media being a dominant part of people’s everyday personal and working lives, it is important to be aware of the security vulnerabilities that social platforms pose. Use these insights to improve your social media security.
Social media is a huge part of our lives, from your personal account that allows you to scroll through your feed to businesses using the social media platforms and software packages to connect with customers. Although a useful addition to society, social media can also pose security risks to everyone who uses it.
Hackers understand that millions of people log into their social media accounts daily, offering ample opportunity for them to mine for data. Worryingly, a reported 1.5 billion Facebook users have had their private and personal information sold by hackers. We must do what we can to protect ourselves against the horde of social media threats, and these are the biggest risks to keep your eyes peeled for in 2023.
Looking to improve your social media presence? Check out Top Design Firms’ list of leading social media consultants.
Need help selecting a company?
Based on your budget, timeline, and specifications we can help you build a shortlist of companies that perfectly matches your project needs. Get started by submitting your project details.
Social Media Security Vulnerabilities
- Phishing
- Social engineering
- Clickjacking
- Digital housekeeping
- Fake giveaways and affiliate scams
- News in a vacuum
Phishing
It’s nothing new but phishing remains one of the biggest online threats due to its success rate. Phishing accounts for around 90% of data breaches and we must remain vigilant against them.
On social media, phishing attacks commonly occur when a hacker sends you an email acting as a reputable social media platform. Users are alerted to an ‘issue with their account’ and encouraged to click a link to resolve the problem. Once that link has been clicked, you are commonly led to a fake website infected with spyware to steal your login credentials and use that to hack your other accounts.
Given the sophisticated nature of some phishing attacks, they can either be hard to spot or really obvious. As such, it’s best to remain vigilant with all unsolicited communications and treat them with caution. If in doubt about the validity of any communication from social media platforms, contact their support lines to check whether the message you received was legitimate.
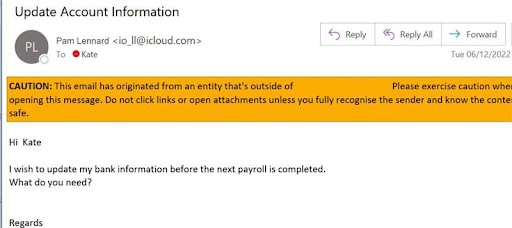
Companies need to be consistently on their guard to detect the increasing sophistication of scams that infiltrate company’s payroll and finance departments as they continue to evolve. With people being more visible and more information shared in the public domain, the easier it is to create a scam and make their attempts to defraud businesses appear more plausible.
Social Engineering
There are other just as damaging ways to disrupt and penetrate a firm’s security systems. One example related to phishing, and many cyberthreats, is social engineering. This term is growing in popularity as it is concerned with any cyberattack that deliberately tricks users into compromising their personal data, whether they unknowingly offer it up to hackers themselves or inadvertently.
Whether it’s a phishing email or a smishing text message, it’s important to remember to never give out any information to unwanted sources.
There is no way to know if the other person responsible for these messages is legit and you could be the target of a social engineering attempt. Once more, if anyone is asking for your information from an unverified source, go straight to that company and speak with customer services to determine its legitimacy.
While social media is an incredible resource for engaging and building a trusted relationship with virtual customers, the online vulnerabilities that come from a shared communal online space need to be mitigated to protect both the business and the consumer.
Clickjacking
While some social media vulnerabilities are easy for hackers to create, others take more effort in coding but still bear fruit. Clickjacking is one such complicated means for hackers to gather your data via social media. It works similarly to phishing but hijacks clicks or ‘likes’ made on social media posts.
Clickjacking hackers use an overlay of the web page you wish to browse with an iframe, tricking you into clicking on their link. These can be very hard to spot as they make use of hidden buttons on your screen to automatically share a post on your profile or download harmful software onto your device.
Digital Housekeeping
Since platforms like YouTube and Instagram began making household names of ordinary people, content creation has seen a boom in popularity. Not only must content creators focus on being authentic, knowing their audiences and staying consistent, they must also stay focused on the cyber threats posed to them.
There is a reason why traditional celebrities make homes for themselves in remote locations or in gated communities – to protect themselves from threats. Social media influencers and content creators must do the same but when inviting people into their homes, their focus must be on digital security. As such, content creators and influencers must protect their private information from being inadvertently shared through the videos and images they create.
That means avoiding all references to where they live and ensuring the background of their videos is non-identifying. Influencers must also take threats made by trolls seriously, reporting them to the authorities and platforms.
Fake Giveaways & Affiliate Scams
Hackers aren’t ignorant of the issues affecting the world and with people facing difficult economic situations, there is an opportunity to exploit people. There are two ways social media users can fall victim to threat actors who appear to be promoting a generous offer: affiliate scams and fake giveaways.
Affiliate scams allow hackers to sell information gained from fake promotional adverts that require personal emails, addresses and phone numbers for a chance to win. Once the information has been acquired, the promotion becomes non-responsive and your data is sold to the highest bidder.
Fake giveaways are similar but take the form of fake competitions or giveaways – the type where you bid a nominal amount for the chance to win a prize worth thousands. Your banking information is collected, allowing the hacker to pay themselves rather than going through a middleman.
News in a Vacuum
Cybersecurity is a significant concern for social media users as hackers become more prevalent. There are also concerns for social media users, who are frequently at the mercy of their chosen platform’s algorithm, tailoring content to what is perceived to be in their interest range.
However, this can provide news and information in a vacuum, amplifying and reinforcing thoughts rather than helping to provide a balanced view of the latest issues. With many elections held in countries across the world in 2023, we are more likely to find ourselves the targets of disinformation campaigns.
As such, large social media platforms like TikTok and Twitter could be forced to disclose their codes to stop young people from being served polarizing and extreme news, The Financial Times reports. Greater awareness of the dangers of the content we consume on social media is potentially on the way for 2023, which can only be a good thing.
Meanwhile, with social media marketing being such a powerful tool for success, social media software packages and channels must also protect themselves against overfamiliar visitors.
Using Social Media To Our Benefit
Social media isn’t all bad. Despite the threats facing users in 2023, social media can also be part of the solution against hackers and cybercrime. Many of the latest threats and news breaks on Twitter, LinkedIn or the blogs of cybersecurity experts and companies.
As such, social media can be your source of information to remain aware of the developing threats online. Following cybersecurity experts, companies, news outlets and influencers provide real-time information on threats and help boost your awareness of things to look out for and avoid.
Additional reading
Need help selecting a company?
Based on your budget, timeline, and specifications we can help you build a shortlist of companies that perfectly matches your project needs. Get started by submitting your project details.